Puppet + Passenger
Puppet is a configuration management tool, its been under heavy development for almost five years now. It became a major open source project in the last few years, surrounded by a large community.
In most of the current environments Puppet Masters will either run on webrick or for the larger environments mongrel was quite standard for a while now.
But Puppet is as well able to be run from within Apache or Nginx. Then you would be using mod_rails (aka. Phusion Passenger). This solution is known to scale best, but was always a bit bulky to install.
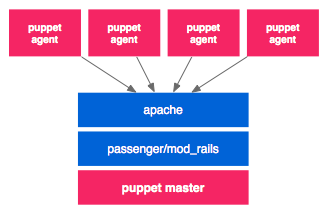
Debian's Puppet package maintainers have prepared the puppetmaster package in Squeeze for an easy installation with mod_rails, so I think this could get the new standard way to install the puppet server.
Rescently the Debian project announced the freeze on its testing branch (codename "Squeeze") which in consequence means that: no more new features will be added and all work will be consentrated on polishing testing up to production level.
I thought it to be a good time then to prepare the "Squeeze" upgrade of my puppet servers and write a short article about it.
Install the packages:
aptitude install puppetmaster libapache2-mod-passenger
Enable the Apache Modules:
a2enmod headers a2enmod ssl
Manually change config.ru
Update: Meanwhile you can skip this step.
I had to manually fix the Rackup-file which comes with the squeeze
puppetmaster package. This file contains logic for initializing puppetmaster
as a rack application. It still tries to initialize puppetmaster,
although the puppet server component was renamed to master.
There is already a open Debian bug for this, and should get fixed until
the final release.
Now change /usr/share/puppet/rack/puppetmasterd/config.ru to:
# a config.ru, for use with every rack-compatible webserver. # SSL needs to be handled outside this, though. # if puppet is not in your RUBYLIB: # $:.unshift('/opt/puppet/lib') $0 = "puppetmasterd" require 'puppet' # if you want debugging: # ARGV << "--debug" ARGV << "--rack" require 'puppet/application/master' # we're usually running inside a Rack::Builder.new {} block, # therefore we need to call run *here*. run Puppet::Application[:master].run
Configure Puppet
When you lounch Puppet the first time, it will generate the SSL certificates. Make sure you configured the puppet certname option to fit your hostname.
If puppetmaster started before you configured it, you can simply delete the ssl directory (/var/lib/puppet/ssl) and restart the puppet master. It will regenerate the directory automatically.
The following represents my puppet configuration in /etc/puppet/puppet.conf.
[main] logdir=/var/log/puppet vardir=/var/lib/puppet ssldir=/var/lib/puppet/ssl rundir=/var/run/puppet factpath=$vardir/lib/facter templatedir=$confdir/templates [master] certname=puppet.ono.at ssl_client_header=SSL_CLIENT_S_DN ssl_client_verify_header=SSL_CLIENT_VERIFY [agent] server=puppet.ono.at [cert] autosign=false
After the certificates are generated, you should disable the puppetmaster daemon in /etc/default/puppetmaster by setting $START from yes to no.
Apache Configuration
Finally configure an Apache virtual host to listen on port 8140 and point it to the ssl certificates generated by puppet. Put the following configuration in /etc/apache2/sites-available/puppetmaster:
## Puppetmaster Apache Vhost Configuration ## Passenger Limits PassengerHighPerformance on PassengerMaxPoolSize 12 PassengerPoolIdleTime 1500 # PassengerMaxRequests 1000 PassengerStatThrottleRate 120 RackAutoDetect Off RailsAutoDetect Off Listen 8140ServerName puppet.ono.at SSLEngine on SSLCipherSuite SSLv2:-LOW:-EXPORT:RC4+RSA SSLCertificateFile /var/lib/puppet/ssl/certs/puppet.ono.at.pem SSLCertificateKeyFile /var/lib/puppet/ssl/private_keys/puppet.ono.at.pem SSLCertificateChainFile /var/lib/puppet/ssl/ca/ca_crt.pem SSLCACertificateFile /var/lib/puppet/ssl/ca/ca_crt.pem ## CRL checking should be enabled; if you have problems with ## Apache complaining about the CRL, disable the next line SSLCARevocationFile /var/lib/puppet/ssl/ca/ca_crl.pem SSLVerifyClient optional SSLVerifyDepth 1 SSLOptions +StdEnvVars ## The following client headers allow the same configuration ## to work with Pound. RequestHeader set X-SSL-Subject %{SSL_CLIENT_S_DN}e RequestHeader set X-Client-DN %{SSL_CLIENT_S_DN}e RequestHeader set X-Client-Verify %{SSL_CLIENT_VERIFY}e RackAutoDetect On DocumentRoot /usr/share/puppet/rack/puppetmasterd/public Options None AllowOverride None Order allow,deny allow from all
Now enable the virtual host configuration, enable all required modules and restart the Apache daemon:
a2ensite puppetmaster a2enmod header a2enmode passenger apache2ctl configtest apache2ctl restart
Final Step - Test
After everything is in place, please test your setup. Open up a web browser and point it to the following Url [adapt the hostname]:
https://puppet.ono.at:8140
You should see a line stating:
"The environment must be purely alphanumeric, not ''"
read more